If you've received email from me recently, there's a good chance it's arrived with a funny-looking header and footer. At the top, it will say
-----BEGIN PGP SIGNED MESSAGE-----And at the bottom is something like this:
Hash: SHA1
-----BEGIN PGP SIGNATURE-----This all looks like nonsense. Has rage and bitterness finally won the battle for Ian's soul, leaving him banging the keyboard randomly while shouting obscenities at the Internet? No! Well, not yet anyways. This stuff around the message is a PGP signature.
Version: GnuPG v1.4.7 (GNU/Linux)
Comment: Promote trust on the internet - Use PGP!
Comment: http://enigmail.mozdev.org
iD8DBQFIqfcGDTFvtHdOkUcRAm4JAJ4vJrcQcAM7gtzoHbI8ul3bA7EUagCcC5aO
RLpYAOHP5YS40I0xSB89pDA=
=VHP3
-----END PGP SIGNATURE-----
If I were to send you a letter or write you a check (hypothetically of course, I hate you all and you certainly aren't getting any of my money), at the bottom there would be a little scribble vaguely resembling my name, as penned by a somewhat slow seven-year-old learning cursive for the first time. This signature is the conventional way of saying "hey, it's really me, your old pal Ian, and I did write this."
A PGP signature serves the exact same purpose for electronic communication. Of course, a string of letters proves nothing. But when I open a signed message in Thunderbird with the Enigmail extension installed, it looks something like this instead:
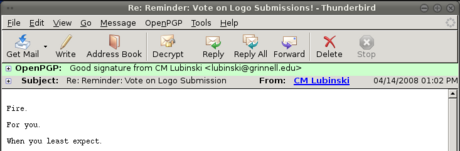
That's nice, innit? That green bar means that I can have confidence that these somewhat unsettling threats are, in fact, from CM Lubinski, and he has electronically signed his name to them.
Ok, so you're probably thinking that this is mildly interesting so far, kind of like a poorly-drafted version of Wikipedia, and it sure beats calculus or mopping the kitchen floor or whatever you ought to be doing, but, well, big deal. Dorks like Ian can get all excited about this PGP thing, but you're going to go trawl YouTube for some clips of a baby rabbit eating its own poo. You don't need all this signature stuff, right? Wait! That furry redigester will be there in ten minutes. First, read about...
Why You Need PGP
You need PGP. You're complacent. Things are going smoothly on the internet. Your biggest problem most of the time is the occasional piece of spam that slips through the filters and annoys us for the ten seconds it takes to read "Fr33 V1agr@" and click Delete. But the convenience of technology hides an ugly truth: email is horribly, horribly insecure.Right now, right this instant, I could send you a message purporting to be absolutely anyone. It doesn't even take that diploma sitting on my bookshelves to do it. The Grinnell mail server and a dirty trick (which I am not going to share) is sufficient. Oh look, good old Rupert sent me something just now:
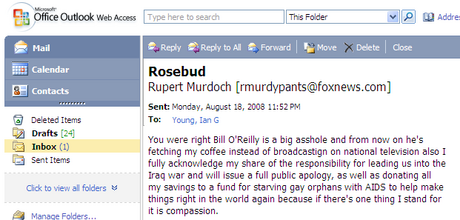
I (or someone with considerably worse intentions) can pretend to be anyone in email. To illustrate my point further, here's an email coming from a domain name that doesn't even exist (I checked):
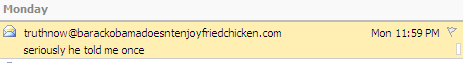
It doesn't have to be imaginary email addresses either. I could send a message with a bunch of inappropriate jokes to your boss that looks like it's from you. I promise I'm not going to, but I, or anyone else, could. That's scary stuff. We've seen the tip of the iceberg on this with phishing emails that look like they come from accounts@ebay.com or whatever. People click those fake links by the boatloads and compromise all sorts of financial information. Even smart, internet-savvy people do. Why? Because we're complacent, and no one ever taught us to doubt that the person in the From: field actually sent that message.
Encryption
Scared yet? Here's some more food for thought: ever send private information through email? Like, say, financial information, or your company's business deals, or those emails you get when you register an account somewhere that sometimes have your new password in them. Or even just personal correspondence that you don't want to share with anyone except the recipient.Guess what - everything you send in email winds its way across the internet in "plain text" - meaning, anyone who looks can read it. If any link in the chain of servers and data lines between you and your recipient is compromised - like someone eavesdropping at your wireless hotspot, or a mail server that's been broken into by hackers, or someone tapping an ethernet line somewhere, or a spying government aided by crony telecoms - all your email is sitting there waiting to be poked through. Additionally, there's very little oversight of how mail servers (of which any given message may cross through quite a few) are administered, so it's quite possible that your messages will end up sitting on the server or on backup tapes for a long time - quite possibly years.
My point is this: we have no reason to be certain that everyone who gets a look at our email is trustworthy, and yet we send everything totally unprotected from prying eyes. It's like sending all of your bank deposits and love letters on postcards when some of the postmen have no credentials and didn't even pass a background check to get the job.
Luckily, PGP also provides optional encryption. It's like the electronic version of a security envelope. An encrypted messages looks like garbage, just a string of nonsensical letters. It's only when your intended recipient decrypts the message that it becomes readable again.
How PGP Works (the short version)
I want to give a brief overview of how PGP works. This isn't going to be the technical version (I'm not even qualified to give the technical version). It's also not going to be a guide to setting up your computer to use PGP. For that I simply direct you to the two plugins I use and like: Enigmail and FireGPG, and especially the quick start guide for Enigmail, which is really stellar and walks you through the steps of setting it up and using PGP for the first time. In this article, I just want to explain the underlying concepts so you can see how PGP works, and why it's such a great idea.To start using PGP, you create a "key pair," which consists of two parts, a public key and a private key. Your public key is something you can give to everyone - you can email it as a file, put it somewhere online, upload it to a keyserver (try searching for my name or email address), whatever. Your private key, as the name suggests, you keep to yourself - it's usually password protected as an additional layer of security. These two keys are tied mathematically. I don't pretend to understand all the details, but it's something to do with factoring primes, and the important point is that it's very quick to go one direction, but incredibly difficult to go the other. So while someone could, in theory, guess your private key using only your public key, it would take the world's fastest hardware thousands of years (yes, human years) to do so. Basically, these keys are pretty secure.
Now, when you write an email and sign it with PGP, the program uses your private key to create a string of letters that is algorithmically tied to the contents of your message. When someone receives your message and wants to verify that it came from you, they take your public key and reverse the process, checking the signature against the message. Verifying a PGP signature assures you that the message came from the owner of the key because only the person with access to the private key could have created that signature. When you want to encrypt something, you take your recipient's public key and use that to turn the message into gobbledygook. That way, only the person with access to the private half of that key (i.e. your intended recipient) will be able to decrypt and read the message.
A Brief Interlude on Trust
There's one more feature of PGP I want to touch on briefly, because I think it's pretty cool: the concept of trust.I've been going on and on about how secure PGP is, but there's a hole in all this: how do you get other people's keys in the first place? After all, just because someone puts a key up on a public keyserver saying they're James T. Madison, you have no proof that that's actually who made that key. If you downloaded the key from that person's personal website or imported it the first time they sent you a signed message, you might trust that it's who you think it is. If they gave you the key in person, say, printed on a business card, you might trust it a whole lot more. But of course, it's not feasible to get all your keys in person - email is supposed to be convenient.
Keeping that in mind, let's do a quick thought experiment. In real life, you trust Bill because you've been friends with him for ten years and he's always been reliable and honest. Bill has a friend, Jack, who you have never met. But Bill vouches for Jack, and since you trust Bill, you trust Jack (to a certain extent).
PGP has functionality that emulates these sorts of relationships - the phrase "webs of trust" gets used a lot. When you import someone else's key, you can specify how much you trust that key. And, if you choose, you can sign other people's public keys, which is like vouching that they are who they claim to be. So suppose I have complete trust that John Stone's key is legit, because I got it from him in person. I sign Stone's public key. Now maybe CM just pulled Stone's key off a public server. He doesn't know if he should trust it or not. But say CM already trusts my key - since he trusts me and I have signed (vouched for) Stone's key, CM's PGP program knows that Stone's key is reasonably trustworthy.
The Future of Trust
Stop and think about webs of trust for a second. Isn't it a cool idea? This is the power of social bonds, realized in electronic form. Picture a world where everyone uses PGP. Imagine how hard it would become for frauds to work their way into a position to do any real damage when no one will vouch for them. Imagine the freedom to trust, really trust, people on the Internet. This is where I think PGP could take us.One More Time, Why?
Okay, so I think PGP is important. But why am I signing all my emails with it, when next to none of my recipients are currently equipped to handle it? I have several reasons, most of which are inspired by John Stone's opinions on this topic:- Someone's gotta do it. If we all hang around waiting for other people to use PGP first, it will never happen. By signing my messages with PGP, the benefits are immediately available to anyone who sets it up and imports my key.
- Advertising the functionality. Sending signed messages advertises my public key. If you want to send me an encrypted message, you know I am equipped to handle it, and you can pull my public key from the signed message to use for encrypting.
- Proselytizing. This is probably my biggest reason for signing at the moment, and is also my reason for writing this post. I hope that some small percentage of people who receive my signed messages will, rather than being confused or just ignoring the extra stuff, be curious and look into PGP, and maybe realize what a great thing it is. I plan to link to this post in the comment section of the signature, in hopes of furthering this goal.



1 comment:
You've convinced me.
Post a Comment